Accept crypto with CoinGate
Accept crypto with confidence using everything you need in one platform.
What is RDP? Remote Desktop Protocol Explained 2025
Uncover the capabilities of Remote Desktop Protocol (RDP), a technology that lets you connect to and control another computer remotely.
This guide will help you understand how RDP works, its real-world applications, security measures, and more. Whether you’re new to RDP or looking to enhance your knowledge, you’ll find everything you need right here.
Be sure to also check out the best RDP providers that also take payments in crypto.
What is RDP? Everything You Need to Know
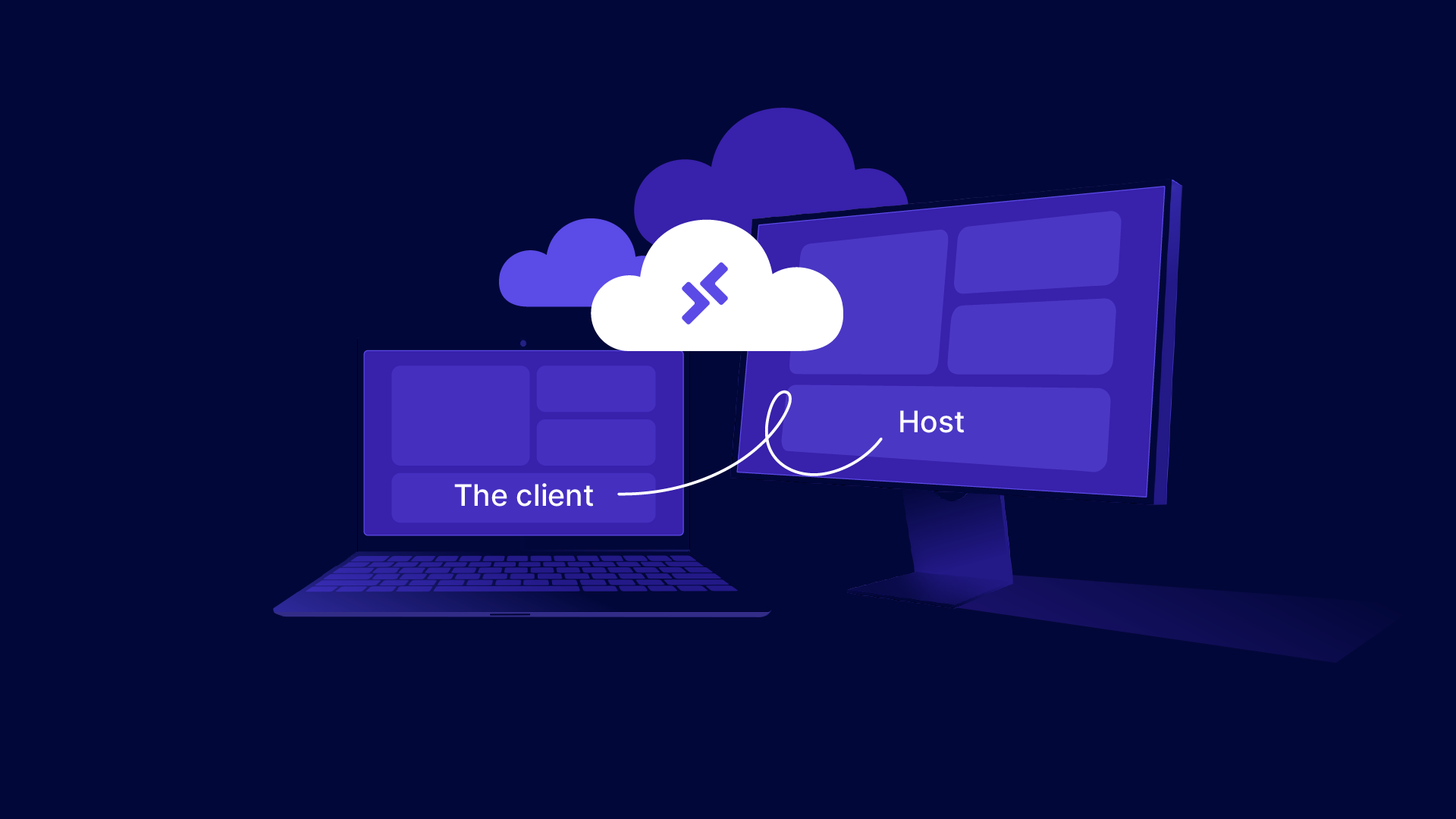
Remote Desktop Protocol (RDP) is a technology that enables computer users to connect to and control another computer remotely.
This protocol is essential for allowing one computer (the client) to display the desktop and run applications of another computer (the host) over a network connection.
Initially, understanding the role of RDP may seem confusing, that’s why, in this short article you’ll learn about the following:
- How does RDP (Remote Desktop Protocol) work?
- Remote desktop properties
- What are Remote Desktop Protocols Used For? Real Use Cases
- Recommendations for the Best RDP Providers
- 10 Steps to Remote Desktop Access Security
- Pros and Cons of RDP
- Remote Desktop Connection Overview
- FAQs
How Does RDP Work? Here’s a Simple Breakdown
Connection Setup
RDP operates by establishing a remote network connection between a client computer and a host computer.
The client uses RDP server software to initiate a connection request, which the host must accept. This connection can be made over the Internet or through a local network, depending on the RDP client software setup.
Display and Interaction
Once the connection is established via the remote desktop software, the desktop interface of the host computer is transmitted over the network to the client computer’s display.
This allows the user at the client computer to see and interact with the host computer’s desktop environment as if it were local. The client can open files, use applications, and manage settings remotely.
Data Transmission
Interaction details such as mouse clicks, keyboard inputs, and other commands are sent from the client to the host, where they are executed. Responses from the host, including graphical updates, are then sent back to the client.
This two-way communication happens quickly to ensure a smooth user experience as if the user were directly interacting with the host machine.
Remote Desktop Properties
Remote Desktop Protocol (RDP) is equipped with a variety of properties that enhance its functionality and security, making it a robust tool for remote desktop access and management.
Here’s a detailed look at these properties and how they benefit users:
Enhanced Security and Authentication
RDP supports smart card authentication, providing a secure method of verifying a user’s identity before granting access to the remote system. Additionally, it uses 128-bit RC4 encryption to secure mouse and keyboard data, ensuring that sensitive information remains protected during transmission.
For further security, RDP also supports Transport Layer Security (TLS), which safeguards the data transmission against interception and tampering.
Performance Optimization
Understanding the need for efficient use of bandwidth, a Remote Desktop Protocol connection includes a bandwidth reduction feature. This is particularly beneficial for users with low-speed internet connections, as it optimizes the data transfer rate to ensure smoother remote desktop interactions.
RemoteFX virtualized GPU support is another significant property that enhances graphical output and overall performance, making it ideal for applications that require high graphical processing capabilities.
Versatility in Access and Control
RDP allows the use of multiple displays, enhancing productivity by expanding the workspace across several monitors.
Users can also disconnect temporarily from the remote desktop protocol without having to log off, preserving the session’s state until they reconnect. This is useful for maintaining long-running tasks or processes.
Local Resource Redirection
One of the standout features of having a Remote Desktop Protocol is its ability to redirect local files, printers, and ports to the remote desktop. This means that applications running in a remote desktop session can access local files, utilize local printers, and communicate with devices connected to local ports.
Furthermore, it directs audio from the remote desktop to the user’s local computer and shares the clipboard between the local and remote computers, facilitating seamless data and multimedia exchange.
Application Flexibility
RDP enhances user experience by allowing applications on a remote desktop to run on a local computer. This capability is bolstered by improvements to RemoteApp, which make it easier to use remote applications alongside local ones, creating a cohesive workspace.
The protocol can support up to 64,000 independent channels for data transmission, with the option to encrypt data using 128-bit keys, highlighting its capability to handle extensive data exchanges securely and efficiently.
Considerations
While RDP is feature-rich, it is important to note that not every RDP client supports all these features comprehensively. The availability and performance of certain features can also depend on whether the client is operating in enhanced session mode.
Together, these properties make RDP a powerful tool for businesses and IT professionals who require reliable, secure, and efficient remote desktop access solutions.
Whether managing server farms or providing remote support, RDP’s capabilities can be tailored to meet diverse needs, making it a cornerstone of modern IT operations.
What are Remote Desktop Protocols Used For? Real Use Cases
Remote Desktop Protocol serves a variety of use cases across different fields and industries, using its flexibility to provide remote access to a computer’s desktop environment.
Here are some of the primary use cases for RDP:
Remote Work
Access to Workstations – Employees can remotely access their office computers from anywhere, allowing them to use their work environment, applications, and files just as they would if they were physically present in the office.
This is especially useful for organizations with flexible working policies or those who need to maintain business continuity during disruptions such as inclement weather or health-related closures.
IT Support and Management
Troubleshooting and Maintenance – IT support teams frequently use RDP to remotely connect to users’ computers to diagnose and resolve system issues.
This remote support capability reduces the need for in-person visits, saving time and resources while improving response times for resolving IT issues.
System Updates, Patches, and Administration – IT administrators use RDP to remotely administer servers and desktops, applying updates, patches, and configuration changes required to maintain IT infrastructure and ensure security and performance.
Education and Training
Remote Instruction – Educators and trainers can use RDP to access educational software hosted on school servers, demonstrating processes and software used by students working remotely. This capability is particularly valuable in distance learning environments where students and teachers are not in the same location.
Lab Access – Students in fields such as computer science or graphic design can remotely access lab computers equipped with specialized software needed for coursework, enabling practical experience without physical presence in a lab.
Software Development and Testing
Development Environments – Developers can use a Remote Desktop Protocol to access development environments hosted on remote servers. This allows them to work from anywhere while taking advantage of powerful server resources that might not be available on their local machines.
Application Testing – RDP enables testers to remotely access various environments and platforms to test software applications under different scenarios, ensuring compatibility and performance across diverse systems.
Healthcare
Remote Medical Analysis and Reporting – Healthcare professionals can use RDP to access medical applications and patient records remotely to perform analyses and prepare reports without being on site, which is vital for timely medical consultations and treatments.
Business Continuity
Disaster Recovery – In the event of a disaster that impacts physical business locations, RDP can be a critical component of a business continuity plan, enabling staff to continue operations remotely by accessing critical applications and data stored on off-site servers.
Manufacturing and Engineering
Remote Monitoring and Control of Manufacturing Processes – Engineers and technicians use RDP to monitor and control industrial machines and processes remotely. This helps in optimizing production efficiency and troubleshooting without being physically present on the factory floor.
Access to High-Performance Computing
Resource-Intensive Applications – Users who require high-performance computing resources for tasks such as video editing, 3D rendering, or large-scale simulations can use RDP to remotely access powerful machines that can handle such resource-intensive applications more efficiently than typical personal computers.
By providing a means to access and control computers remotely, RDP not only enhances productivity and flexibility but also plays a crucial role in modern IT strategies, educational methods, and business operations. Its versatility makes it a fundamental tool in many technological environments.
Recommendations for the Best RDP Providers

Here are some recommendations for quality RDP services that might suit your needs perfectly. All these RDP providers accept digital token payments through our cryptocurrency payment gateway:
HomeRDP
HomeRDP offers dedicated RDP services with Bitcoin payments. Enjoy instant activation, 24/7 live support, and unlimited bandwidth.
Plans cater to various needs and budgets. The “Cheap Admin RDP” starts at $9.99/month with 1vCPU, 2 GB RAM, and 15 GB SSD. For high performance, the $149/month plan includes a Ryzen™ 9 processor, 128GB RAM, and 4TB SSD.
Global servers ensure optimal connectivity. Specialized plans for Android emulation and Forex trading. Clear refund policies and free admin control panels enhance user experience. A smart choice for RDP with Bitcoin.
GPURDP
GPURDP offers GPU-powered servers, ideal for heavy graphical tasks. Starting at $169/month, services include Nvidia GTX 1080, 64GB RAM, and 1TB SSD.
They guarantee 99.9% uptime and provide a money-back guarantee. Plans are tailored for Android emulators, gaming, and streaming. With over 300 positive reviews and 5 years of operation, GPURDP is a reliable choice for GPU servers.
Looking for more options? Check out top 7 RDP services.
10 Steps to Remote Desktop Access Security
For a secure Remote Desktop Protocol (RDP) experience, assessing and implementing robust security measures is crucial for preventing brute force attacks, data breaches, and unauthorized access.
Here are some best practices to enhance RDP security effectively:
#1 – Strong Authentication
Implement strong passwords combined with multifactor authentication (MFA) to secure Remote Desktop Protocol access.
This approach helps to safeguard a remote computer against unauthorized entry by adding an additional layer of security beyond just the password.
#2 – Access Control
Restrict RDP access strictly to authorized remote users. Avoid using default administrator accounts, which are often targeted by attackers. Instead, create specific user accounts with the necessary permissions to reduce potential security risks.
#3 – Network-Level Authentication (NLA)
Enabling NLA adds a preliminary authentication step before establishing a Remote Desktop Protocol session. This significantly enhances security by ensuring that user credentials are verified prior to starting any session.
#4 – Encryption
Set RDP data transmission encryption to ‘High’ to protect sensitive information during transmission.
This encryption prevents eavesdropping and ensures that data remains secure between the client and the server.
#5 – Rename Default Administrator Accounts
By renaming default administrator accounts, you reduce their visibility as targets for cyber attacks. This simple step can greatly deter automated hacking attempts.
#6 – Disable Clipboard and Printer Redirection
To prevent potential data leakage and protect against driver-based attacks, disable clipboard and printer redirection features in Remote Desktop connection sessions.
These features, while convenient, can be exploited to extract data or introduce malicious code.
#7 – Remote Desktop Access Session Management
Implement controls to limit the number of simultaneous sessions each user can establish. This helps in preventing abuse of the system and ensures that resources are used efficiently and securely at all times.
#8 – Regular Updates
Take Note! It’s essential to keep your software and systems up to date.
Be sure to regularly install security patches and updates for RDP and related systems to guard against known security risks.
#9 – Monitor Activity
Establish a robust monitoring system using logs and auditing tools to track Remote Desktop connection activity. Monitoring helps with the early detection of suspicious behavior and potential security breaches.
#10 – Avoid Internet Exposure
Direct exposure of RDP to the internet significantly increases the risk of cyber attacks. Instead, make sure to use a Virtual Private Network (VPN) or other secure methods for remote access. VPNs and other enhancements provide encrypted channels and additional security.
And finally, strictly adhering to these best practices ensures that RDP usage remains secure and efficient, safeguarding your remote desktops and systems against unauthorized access and potential security threats.
Pros and Cons of RDP
Pros of RDP
- Accessibility – Provides remote access to workplace or home PCs from anywhere globally, enhancing productivity and flexibility.
- Cost-effective – Reduces the need for physical IT presence and enables efficient remote support, lowering operational costs.
- Feature-rich – Supports advanced features like clipboard sharing, printer redirection, and high-quality graphics and audio.
Cons of RDP
- Security Vulnerabilities – If not properly configured, a Remote Desktop connection can expose systems to security risks, such as unauthorized access and data breaches.
- Performance Issues – On slow networks, a Remote Desktop connection can suffer from latency and performance degradation, impacting the user experience.
- Complexity in Setup – For higher security setups, configuring RDP with VPNs and other security measures can be complex and require technical expertise.
Remote Desktop Connection Overview
Remote Desktop Protocol (RDP) is a critical technology that allows remote control of computers for multiple purposes, from security and maintenance to business continuity and software development.
It gives computer users the convenience of accessing their work environment from any location. RDP offers them a secure network connection to interact with remote systems as if they were sitting right in the same room.
This not only enhances productivity but also supports a diverse range of applications from IT management to remote education, making it an indispensable tool across multiple disciplines.
However, while a Remote Desktop Connection offers remarkable benefits such as operational efficiency and flexibility, it also presents challenges, particularly regarding security.
Vulnerabilities can expose remote users to risks like brute force attacks, data breaches and unauthorized access if proper security measures, including strong authentication protocols, updated software, and secure networking practices, are not common practice.
Users must prioritize these security practices to protect their data and maintain the integrity of their remote connections.
In summary, the effectiveness of RDP hinges on a balanced approach that maximizes its extensive functionalities while mitigating potential security risks.
By maintaining rigorous security standards and staying informed about best practices, users can apply the benefits of RDP as a powerful tool for remote access, ensuring both productivity and security in their daily work.
The key takeaway is that while RDP transforms remote access by providing extensive control and flexibility, its full potential is realized only when complemented with stringent security measures.
FAQs
Are there alternatives to using RDP for remote desktop access?
Yes, there are several alternatives to RDP for remote desktop access, including VNC (Virtual Network Computing), TeamViewer, and AnyDesk. These tools offer similar functionalities with varying features like cross-platform support, file transfer, and ease of use.
Some may provide enhanced security features or simpler setup processes, catering to different user needs and preferences in remote access solutions.
How many simultaneous users can RDP support?
Windows servers by default support up to two simultaneous Remote Desktop admin connections. If you need to accommodate more users, such as allowing five users to log in simultaneously, you must install the Remote Desktop Session Host Role. This installation expands the capability beyond the standard two-user limit to support additional concurrent connections.
What operating systems support Remote Desktop client connections?
Remote Desktop client connections are supported by several operating systems, including Windows 11 Pro, Windows 11 Enterprise, Windows 10 Pro, Windows 10 Enterprise, and Windows Server versions 2022, 2019, and 2016. These systems allow users to establish and manage Remote Desktop sessions effectively. You can also use Remote Desktop on your Windows, Android, or iOS device to connect to a Windows 10 PC from afar.
Accept crypto with CoinGate
Accept crypto with confidence using everything you need in one platform.

