Accept crypto with CoinGate
Accept crypto with confidence using everything you need in one platform.
How does the cryptomining malware work and how to avoid it?
We live in an exciting world where technology advances at a pace never seen before. Unfortunately, as we get to experience the fascinating rise of innovations like blockchain, Bitcoin and cryptocurrencies in general, we also face new challenges in digital security.
In the past couple of years, crypto-focused cyber attacks have become widespread. It all seemingly started with an increase in numbers of ransomware outbreaks.
By targeting a specific person with phishing attacks, a cybercriminal would eventually take over the control of a computer and ask for a ransom pay (usually in Bitcoin) to unlock the now encrypted private data, or, in other cases, prevent fraudsters from destroying it or making it public on the internet.
This scheme appeared to be a preferred method for swindling the funds out of the pockets of crypto wealthy individuals if done right. Unless the victim has all his data safely backed up, it is also a relatively easy task to execute for an experienced coder who doesn’t mind getting his hands dirty.
However, when we talk crypto and cybercrime, a bigger threat emerges on a global scale, more complicated and even more profitable than ransom tactics – it’s crypto-mining malware or a process called crypto-jacking.
According to the cybersecurity company McAfee, successfully operating crypto-jacking malware numbers has risen by 4000% in the last year, one of the reasons being that it is very cheap to attempt yet might bring massive returns.
It is estimated that for a cybercriminal, a single crypto-jacking software can accumulate up to $750,000 worth of cryptocurrency per month on average, whereas the web-based mining scripts can gather around $30,000 per month. In other words, practically with little-to-no resources, fraudsters can target countless people and companies with multiple invasion methods at the same time, and they do.
What does the crypto-jacking malware do?
Basically, cryptocurrency mining malware stealthily hijacks devices like computers or phones and steals their resources for mining cryptocurrencies. Once activated, such a malicious file can affect individuals as much as large enterprises that rely their operations on networks of countless servers.
Once the crypto-malware connects your device to a particular node together with all other infected devices on a crypto mining botnet, it starts to use the device’s resources to mine cryptocurrencies for the cybercriminal.
Although the virus always forces devices to share small pieces of data between each other and the cybercriminal, such software isn’t usually able to obtain personal data. However, as digital crime is getting more sophisticated, considering that various new threats emerge day by day, you never know how dangerous a specific malware program might be.
There’s also another common form of the crypto hijacking – just by embedding a JavaScript code on the website, a cybercriminal can harness your computer resources for mining digital assets for as long as the webpage remains open. It is called a drive-by crypto mining, or a browser-based crypto mining.
However, this is not considered to be as dangerous because it doesn’t actually put any malicious files on your devices. Still, the act is perceived as unethical by most, especially if the website’s owners do not ask for the user’s consent.
How can your computer get infected with crypto-malware?
There are several ways how hackers can hijack your computer or other devices with a malicious virus.
Phishing attempts
If you ever put your email in shady websites for any reason (like registering an account on odd websites, subscribing to a fake service/newsletter, etc.), it may end up in some public email spam list. And be sure that those who are looking for ways to spread their malicious software will be using these mailing (or spam) lists and possibly target you as a potential victim.
Of course, a cybercriminal can get your email address somewhere else as well. As long as it’s made public, someone can dig it up and try to take advantage of you.
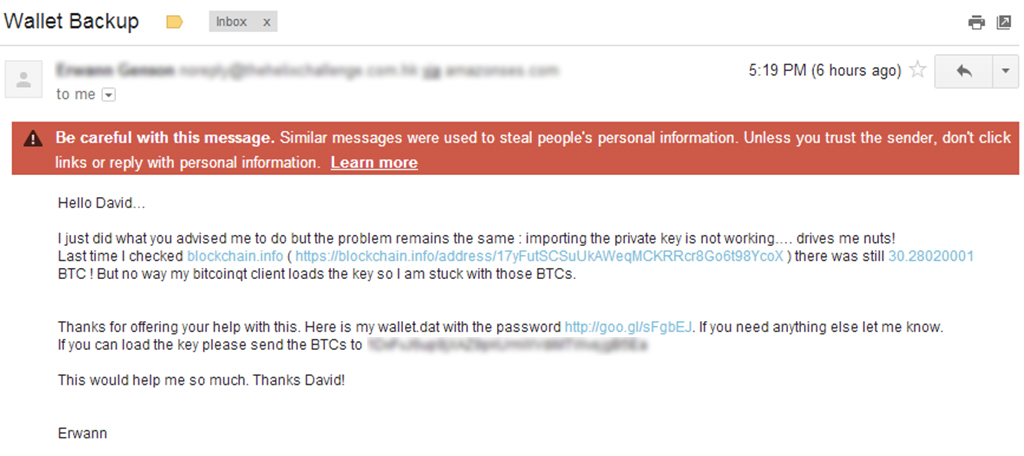
Phishing attempts usually start with well-crafted, although fake emails that push you to click on a malicious link or open an infected email attachment. It could be personal offers from strangers that sound too good to be true, fake warnings and notifications from seemingly legit service providers that you use, and so on.
The chances are that the majority won’t be fooled that easily. However, there is always a small percentage of those who inevitably fall for it, especially if the phishing attack is sophisticated and well thought of. As a result, that is enough to consider the attack successful, meaning profitable.
Infected files
It’s easy to find a random website that would offer free software clients that would otherwise cost money or shady torrent programs that have a little-to-no reputation but can do the job you need to do. Even if you’re looking for a simple tool to use one time, it might be enough to catch a nasty virus.
For example, once my mother asked me to edit her favorite part of the song so she could make a nice phone tune out of it. So, I downloaded a random free audio editor to do this one task, and with it came a hidden malware that was not that easy to get rid of.
It’s also possible to get a virus when installing questionable web browser extensions, downloading illegal files via torrent, using poorly protected apps or opening files attached to an email with an intent to trick people into thinking they’re real.
Social engineering
In the worst-case scenario, a hacker might be a target not thousands of people, but specific persons using social engineering techniques.
This is worse because before the attack, a hacker will try hard to find as much information about you as possible in order to identify your pain points and manipulate you into making certain actions which would result in you losing sensitive data.
In other cases, a scammer might even try and call your bank pretending to be you with an intention to trick the 3rd party services into believing that they are speaking with a real customer, whether to reset account passwords, initiate a bank transfer, etc.
How do I avoid being crypto hijacked?
You can avoid all the troubles if you take measures to protect yourself.
First of all, it’s important to keep your mail email address as private and clean as possible, meaning you shouldn’t share it on websites that seem shady or use it when registering an account in unsafe sites or applications.
Also, always remain sceptical when opening emails that you didn’t expect to get. Look closely whether the content of it makes sense, or if the sender’s email address doesn’t show any red flags. Other than that, think twice before opening any attachments.
In case of avoiding drive-by crypto mining, simply disabling the JavaScript makes it impossible to force crypto mining by visiting websites. Just keep in mind that if you disable it, your browser might not load all the websites correctly. There are also a couple of web browser extensions that effectively block drive-by crypto-mining scripts, such as No Coin or minerBlock.
How do I know if my PC is infected with crypto-malware?
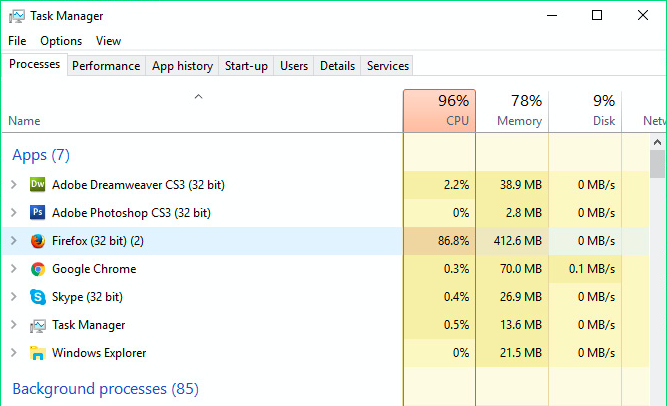
You might notice vague signs pointing out that something is wrong. First, your computer, especially if idle for a while, emits louder sounds than usual and heats up more than it should. Or your laptop drains the battery much faster than not so long ago. The reason for this might be that the malware has already infected your computer and is using your CPU for its own agenda.
Although that’s not always the case, some sophisticated malware programs can scan your computer’s parameters and adapt itself in a way that you won’t be able to tell the difference whether your computer is using more resources than usual.
Sometimes, you might also feel the internet connection breaking for a second or two. This might also indicate that something is not right, considering that your other devices might also be compromised if they are all connected to the same Wi-Fi network.
What do I do if my device is already infected?
If you experience any of these issues, you shouldn’t hesitate to invest in a decent anti-malware software that has strong protection against crypto-oriented malware, such as Malwarebytes, to check and clean up ALL of your devices. It would also be wise to combine your antivirus with other security measures like VPN.
VPN, or Virtual Private Network, is a software that encrypts your data and acts as a bridge between you and your internet provider. It allows connecting to the internet securely and protects your incoming and outgoing data by transmitting it via an encrypted tunnel. The software itself is easy to use and takes only a couple of minutes to set up.
If you’d consider buying a VPN, click here to find the best VPN providers that also accept cryptocurrencies for their services.
However, some viruses are too complex to erase them in a way so that they wouldn’t leave any trace. If you truly want to remain safe, you might have to completely wipe out the hard drive and reset your operating system.
Always stay safe!
Digital security is utmost important, especially now when we’re all entangled with each other in the world wide web like never before. It is even more crucial if you hold a fortune of cryptocurrencies in wallets or exchanges.
Poor security measures can lead to great loses, so don’t think twice when you see a way to improve your protection against mischievous people!
Learn how to protect your devices from the internet threats
With that said, we hope you’ve learned something new today! If you wish to be notified every time we release new content, the easiest way to do it is by subscribing to our blog! Simply enter your email address in a column down below and that’s it!
Accept crypto with CoinGate
Accept crypto with confidence using everything you need in one platform.